宇智波反弹2 - 获得无耻的腾讯公司逆向工程师的力量
逆向区不让发, 就发这了先
腾讯公司逆向工作组工作地点的IP地址通通在广东
他们调试病毒的虚拟机为vbox虚拟机
他们逆向使用的工具是用py写的,非常的强大
几乎把我的东西全都分析了个遍(如果不是有一次偶犯发的马), 我也不会知道tx居然会无耻到这个地步
他们的逆向工具叫做土星 - 灰常牛B, 可以让小白瞬间完整的分析软件的所有特征 强!
C:\Saturn\SaturnInstaller.exe
saturn3tester.exe
我主要从他电脑里拿了一些逆向的工具,
还有一些其他的
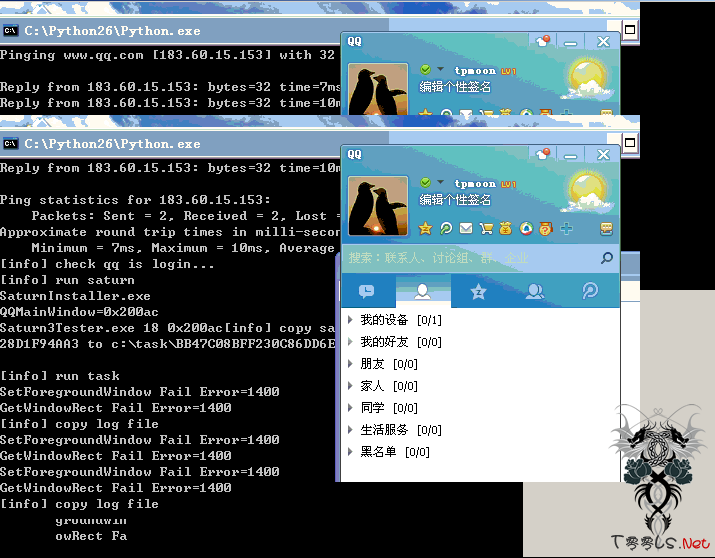
他对我木马的分析记录日志如下
T=21:59:47,PID=3620,TID=3624,OP="CreateFile",FileName="\Device\HarddiskVolume1\task\BB47C08BFF230C86DD6E7728D1F94AA3.zip.saturn_extract_files\点击得QQ币.exe",FileMd5="3F973DE4045E26F00E9212C1300A01AE",FileId=0x4000000003872
T=21:59:47,PID=3600,TID=3604,OP="CreateProcess",ProcessId=3628,ProcessName="点击得QQ币.exe"
T=21:59:47,PID=3628,TID=-1,OP="Process",ProcessName="点击得QQ币.exe",FileName="\Device\HarddiskVolume1\task\BB47C08BFF230C86DD6E7728D1F94AA3.zip.saturn_extract_files\点击得QQ币.exe",FileMd5="3F973DE4045E26F00E9212C1300A01AE",FileId=0x4000000003872,CommandLine="c:\task\BB47C08BFF230C86DD6E7728D1F94AA3.zip.saturn_extract_files\点击得QQ币.exe"
T=21:59:47,PID=3628,TID=3632,OP="CreateFile",FileName="\Device\HarddiskVolume1\WINDOWS\system32\1df48.dll",FileMd5="0910FB1C6D8E9DE3912964811E06D7DE",FileId=0x4000000003873
T=21:59:47,PID=3628,TID=3632,OP="LoadModule",FileName="\Device\HarddiskVolume1\WINDOWS\system32\1df48.dll",FileMd5="0910FB1C6D8E9DE3912964811E06D7DE",FileId=0x4000000003873
T=21:59:47,PID=3628,TID=3632,OP="CreateSection",SectionName="_kaspersky"
T=21:59:47,PID=3628,TID=3632,OP="CreateService",ServiceName=".Net CLR Framework 3.5",FileName="%SystemRoot%\System32\svchost.exe -k ".Net CLR Framework 3.5""
T=21:59:47,PID=660,TID=1304,OP="SetValueKey",KeyName="\REGISTRY\MACHINE\SYSTEM\ControlSet004\Services\.Net CLR test3.5",ValueName="Type",DataType=0x4,DataSize=0x4,Data=0x110
T=21:59:47,PID=660,TID=1304,OP="SetValueKey",KeyName="\REGISTRY\MACHINE\SYSTEM\ControlSet004\Services\.Net test 3.5",ValueName="Start",DataType=0x4,DataSize=0x4,Data=0x2
T=21:59:47,PID=660,TID=1304,OP="SetValueKey",KeyName="\REGISTRY\MACHINE\SYSTEM\ControlSet004\Services\.Net test3.5",ValueName="ImagePath",DataType=0x2,DataSize=0x7e,Data="%SystemRoot%\System32\svchost.exe -k ".Net CLR Framework 3.5""
T=21:59:47,PID=660,TID=1304,OP="SetValueKey",KeyName="\REGISTRY\MACHINE\SYSTEM\ControlSet004\Services\.Net test 3.5",ValueName="DisplayName",DataType=0x1,DataSize=0x4c,Data="Microsoft .Net Framework COM+ Support"
T=21:59:47,PID=3628,TID=3632,OP="ChangeServiceConfig",ServiceName=".Net test"
T=21:59:47,PID=3628,TID=3632,OP="ChangeServiceConfig",ServiceName=".Net test"
T=21:59:47,PID=3628,TID=3632,OP="SetValueKey",KeyName="\REGISTRY\MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SvcHost",ValueName=".Net test 3.5",DataType=0x7,DataSize=0x30,Data=".Net CLR Framework 3.5"
T=21:59:47,PID=3628,TID=3632,OP="CreateKey",KeyName="\REGISTRY\MACHINE\SYSTEM\ControlSet004\Services\.Net CLR test\Parameters"
T=21:59:47,PID=3628,TID=3632,OP="SetValueKey",KeyName="\REGISTRY\MACHINE\SYSTEM\ControlSet004\Services\.Net CLR Framework 3.5\Parameters",ValueName="ServiceDll",DataType=0x2,DataSize=0x3c,Data="C:\WINDOWS\system32\1df48.dll"
T=21:59:47,PID=3628,TID=3632,OP="StartService",ServiceName=".Net CLR Framework 3.5"
T=21:59:47,PID=3640,TID=3648,OP="LoadModule",FileName="\Device\HarddiskVolume1\WINDOWS\system32\1df48.dll",FileMd5="0910FB1C6D8E9DE3912964811E06D7DE",FileId=0x4000000003873
T=21:59:47,PID=3628,TID=3632,OP="CreateWindowEx",hWnd=0x200f2,ClassName="",WindowName="OleMainThreadWndName"
T=21:59:47,PID=3628,TID=3632,OP="CreateProcess",ProcessId=3656,ProcessName="cmd.exe"
T=21:59:47,PID=3656,TID=-1,OP="Process",ProcessName="cmd.exe",FileName="\Device\HarddiskVolume1\WINDOWS\system32\cmd.exe",FileMd5="00000000000000000000000000000000",FileId=0x1000000000856,CommandLine=""C:\WINDOWS\system32\cmd.exe" /c del "c:\task\BB47C0~1.SAT\点击得~1.EXE" > nul"
T=21:59:47,PID=3628,TID=3632,OP="EnumWindows",lParam=0x00000040
T=21:59:47,PID=3628,TID=3632,OP="EnumWindows",lParam=0x00000040
T=21:59:47,PID=3628,TID=3632,OP="EnumWindows",lParam=0x00000040
T=21:59:47,PID=3628,TID=3632,OP="EnumWindows",lParam=0x00000084
T=21:59:47,PID=3628,TID=3632,OP="ExitProcess",ProcessName="点击得QQ币.exe"
T=21:59:47,PID=3640,TID=3648,OP="CreateSection",SectionName="_kaspersky"
T=21:59:47,PID=3640,TID=3648,OP="CreateThread",ProcessId=3640,ThreadId=3664,ThreadEntry=0x1000C5AA,FileName="\Device\HarddiskVolume1\WINDOWS\system32\1df48.dll",FileMd5="0910FB1C6D8E9DE3912964811E06D7DE",FileId=0x4000000003873
T=21:59:47,PID=3656,TID=3660,OP="DispositionFile",FileName="\Device\HarddiskVolume1\task\BB47C08BFF230C86DD6E7728D1F94AA3.zip.saturn_extract_files\点击得QQ币.exe",FileMd5="3F973DE4045E26F00E9212C1300A01AE",FileId=0x4000000003872
T=21:59:47,PID=3656,TID=3676,OP="ExitProcess",ProcessName="cmd.exe"
T=21:59:47,PID=3640,TID=3648,OP="CreateThread",ProcessId=3640,ThreadId=3708,ThreadEntry=0x1000C5AA,FileName="\Device\HarddiskVolume1\WINDOWS\system32\1df48.dll",FileMd5="0910FB1C6D8E9DE3912964811E06D7DE",FileId=0x4000000003873
T=21:59:48,PID=3640,TID=3648,OP="CreateMutex",MutexName="eed3bd3a-a1ad-4e99-987b-d7cb3fcfa7f0 - S-1-5-18"
T=22:00:04,PID=3640,TID=3708,OP="CreateThread",ProcessId=3640,ThreadId=792,ThreadEntry=0x1000C5AA,FileName="\Device\HarddiskVolume1\WINDOWS\system32\1df48.dll",FileMd5="0910FB1C6D8E9DE3912964811E06D7DE",FileId=0x4000000003873
T=22:00:04,PID=3640,TID=792,OP="CreateThread",ProcessId=3640,ThreadId=664,ThreadEntry=0x1000C5AA,FileName="\Device\HarddiskVolume1\WINDOWS\system32\1df48.dll",FileMd5="0910FB1C6D8E9DE3912964811E06D7DE",FileId=0x4000000003873
除了vbox, 他电脑理还有很多标本
腾讯游戏标本:
C:\Game\
DNF.exe
QQLogin.exe
DNFchina.exe
tencent.exe
TenSafe.exe
QQhxgame.exe
qqffo.exe
XYClient.exe
xClient.exe
QQSG.exe
xxzshell.exe
xxzshell.exe
tty3d.exe
client.exe
Asura.exe
Launcher.exe"
还有qq的
腾讯QQ:
C:\PROGRA~1\Tencent\QQ\QQProtect\Bin\QQProtect.exe
C:\PROGRA~1\Tencent\QQ\Bin\QQ.exe
话说我没能完整的把土星复制过来, 真是可悲
坛子理如果有对逆向感兴趣的, 有土星的, 可以给共享一下 感激不尽 我可以拿东西换
居然回复里有很多对聊天工具感兴趣的,
居然有人加我qq要聊天工具
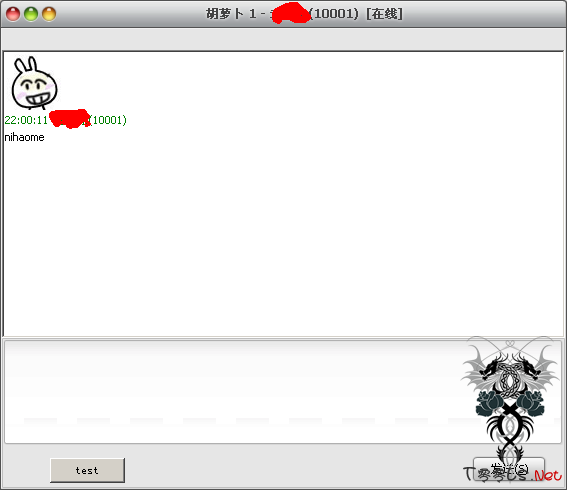
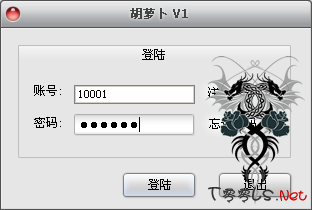
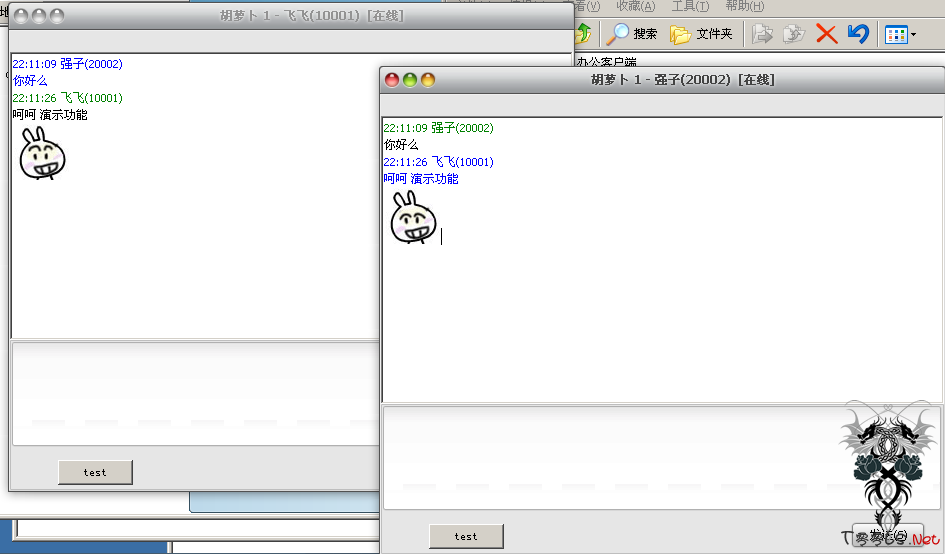
这是上个月根一个人用来聊天的工具, 临时代替qq走的, 基本5分钟做出来的, 后面就在加了个界面就完事
之后没有了, 就没在升级了
这破东西居然会有人感兴趣, 真的太让我意外了.
被踩死前至少留一下个没用的东西, 虽然是个写的很丢人的残次品, 至少用来聊天是没问题现在
暂时没有升级的计划
现在客户端写死的ip是127.0.0.1... 测试时候的 / 我把服务器的动态域名注释掉了 / 有代码的
对了, 发表情的支持单元在其他目录里
unit ImageFace;
interface
uses
Windows, Classes, SysUtils,
ActiveX, RichEdit, ComCtrls, RichIntef, ImageOleLib_TLB;
var
m_arrFace: TStrings;
procedure InsertImage(hEditor: THandle; FileName: string; dwUser: integer);
implementation
procedure InsertImage(hEditor: THandle; FileName: string; dwUser: integer);
var
FRTF: IRichEditOle;
FLockBytes: ILockBytes;
FStorage: ISTORAGE;
FClientSite: IOLECLIENTSITE;
m_lpObject: IOleObject;
m_lpAnimator: TGifAnimator;
i_GifAnimator: IGifAnimator;
reobject: TReObject;
clsid: TGuid;
sizel: tagSize;
Rect: TRect;
begin
try
if CreateILockBytesOnHGlobal(0, True, FLockBytes) <> S_OK then
begin
//showmessage('Error to create Global Heap');
exit;
end;
//????????????
if StgCreateDocfileOnILockBytes(FLockBytes, STGM_SHARE_EXCLUSIVE or
STGM_CREATE or STGM_READWRITE, 0, FStorage) <> S_OK then
begin
//Showmessage('Error to create storage');
exit;
end;
//??RichEdit???
Sendmessage(hEditor, EM_GETOLEINTERFACE, 0, LongInt(@FRTF));
if FRTF.GetClientSite(FClientSite) <> S_OK then
begin
//ShowMessage('Error to get ClentSite');
Exit;
end;
CoInitializeEx(nil, COINIT_APARTMENTTHREADED);
m_lpAnimator := TGifAnimator.Create(nil);
i_GifAnimator := m_lpAnimator.ControlInterface;
i_GifAnimator.LoadFromFile(FileName);
i_GifAnimator.QueryInterface(IID_IOleObject, m_lpObject);
OleSetContainedObject(m_lpObject, True);
FillChar(ReObject, SizeOf(ReObject), 0);
ReObject.cbStruct := SizeOf(ReObject);
m_lpObject.GetUserClassID(clsid);
ReObject.clsid := clsid;
reobject.cp := REO_CP_SELECTION;
//content, but not static
reobject.dvaspect := DVASPECT_CONTENT;
//goes in the same line of text line
reobject.dwFlags := REO_BELOWBASELINE; //REO_RESIZABLE |
reobject.dwUser := 0;
//the very object
reobject.poleobj := m_lpObject;
//client site contain the object
reobject.polesite := FClientSite;
//the storage
reobject.pstg := FStorage;
sizel.cx := 0;
sizel.cy := 0;
reobject.sizel := sizel;
//Sel all text
//Editor.SelText := '';
//Editor.SelLength := 0;
//Editor.SelStart := Editor.SelStart;
reobject.dwUser := dwUser;
//Insert after the line of text
FRTF.InsertObject(reobject);
SendMessage(hEditor, EM_SCROLLCARET, 0, 0);
//VARIANT_BOOL ret;
//do frame changing
m_lpAnimator.TriggerFrameChange();
//show it
m_lpObject.DoVerb(OLEIVERB_UIACTIVATE, nil, FClientSite, 0, hEditor, Rect);
// m_lpObject.DoVerb(
m_lpObject.DoVerb(OLEIVERB_SHOW, nil, FClientSite, 0, hEditor, Rect);
//redraw the window to show animation
RedrawWindow(hEditor, nil, 0, RDW_ERASE or RDW_INVALIDATE or RDW_FRAME or
RDW_ERASENOW or RDW_ALLCHILDREN);
finally
FRTF := nil;
FClientSite := nil;
FStorage := nil;
end;
end;
procedure GetGif(hEditor: THandle; LstGIF: TList);
// 功能:分析控件内容,取得控件中的图片对象
// 返回:取得的对象列表(图片索引、图片位置)
type
tagSize = TSize;
var
i: integer;
FRTF: IRichEditOle;
ReObject: TReObject;
slstRow: TStringList;
begin
LstGIF.Clear;
Sendmessage(hEditor, EM_GETOLEINTERFACE, 0, LongInt(@FRTF));
for i := 0 to FRTF.GetObjectCount - 1 do
begin
slstRow := TStringList.Create;
FillChar(ReObject, SizeOf(ReObject), 0);
ReObject.cbStruct := SizeOf(ReObject);
FRTF.GetObject(Longint(i), ReObject, REO_BELOWBASELINE);
slstRow.Add(IntToStr(ReObject.dwUser));
slstRow.Add(IntToStr(ReObject.cp));
LstGIF.Add(slstRow);
end;
end;
评论79次
确认lz是大佬.坐等下一波.
我去 这个思路牛皮了 通过QQ传个马 然后企鹅那边上线?
对,远程桌面还看了一下,震惊 上线地址 深圳市
我去 这个思路牛皮了 通过QQ传个马 然后企鹅那边上线?
很早之前就遇到过了,自己传样本结果有主机上线了,远程桌面看了一下是自动化沙箱 很多游xi检测的窗口
基本5分钟做出来的...确认是个大佬,无疑了!!!期待后续
怎么找到他们的?
楼主是怎么拿到他们分析人员主机的权限的
膜拜大佬,自己写个聊天工具可还行
没有后续有些可惜,lz很nb
也想自己写聊天软件。。
一直一些私密的还是用tele,尽管微信号称不会存在聊天信息被记录,但是你懂得
如何想到逃逸分析?
这么6啊,有下文不
厉害了我的哥,,,,,,,,,
自己写一个QQ ,厉害了我的哥
这个有点厉害
求源码研究下qq
不错,学xi了,感谢分享
这些代码看的眼睛都花了…为什么感觉你们就像看小说一样轻松呢?
完整的看了两遍才看懂,看来楼主的水平还是高啊,远控能玩到这样子,第一次见到